Information security is not just the configuration of devices, but it broadens out to a perpetual management process. A narrow analysis on a single device does not allow to find out complex attacks, usually extremely dangerous.
Vastalla can provide consulting services on IT security as a whole but also on more specific topics or tools. For instance we can help its Clients find the best value for money SIEM (Security Information and event Management) solution.
Information security is not just the configuration of devices, but it broadens out to a perpetual management process.
A narrow analysis on a single device does not allow to find out complex attacks, usually extremely dangerous. SIEM (Security Information and event Management) must have the whole view of network topology, of infrastructure and of all IT assets involved.
A SIEM solution is critical to a more effective management of all elements. SIEM systems support SOC (Security Operations Center) in daily operation with analysis and events correlation, supplying well-timed alerts.
IT security audit and ISO 27001:2022
Vastalla offers its Clients a structured process that can lead to a ISO 27001:2022 certification. ISO/IEC 27001 is an Information Security Management System (ISMS) standard.
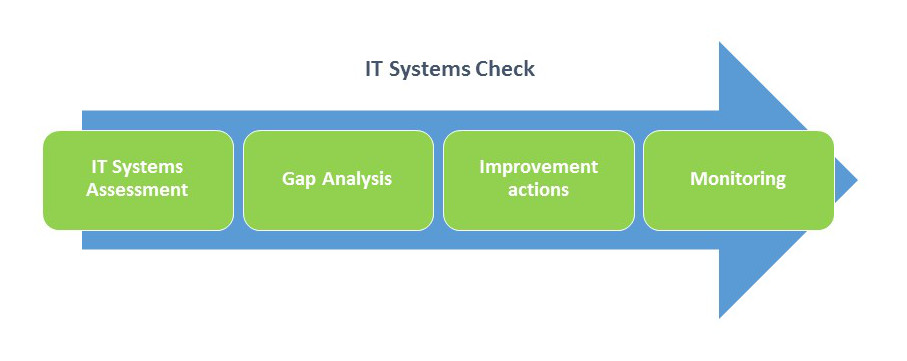
An Information Security Management System must have a strong basis in an accurate IT systems analysis. This analysis must include software applications as well.
Vastalla has a complete offering of services ranging from an IT systems assessment to an accurate Gap Analysis tailored on Clients’ needs and targets. This Gap Analysis is the basis for the successive improvement actions. These improvement actions are then continuosly verified at different stages to guarantee that targets, timetable and efforts are aligned.
After receiving a ISO 27001:2022 certification, our Clients can benefit from:
- scheduled audits that verify that operating procedures are respected as planned; corrective actions are taken in case of misalignments or needed revision of the ISMS;
- low cost dedicated devices that monitor in real time the security status of Clients’ internal systems.